Cisco 642-533 Practice Test, Discount Cisco 642-533 Doc With Low Price
Flydumps presents the highest quality of Cisco 642-533 practice material which helps candidates to pass the Cisco 642-533 exams in the first attempt.The brain dumps are the latest,authenticated by expert and covering each and every aspect of Cisco 642-533 exam.
QUESTION 86
In which three of these ways can you achieve better Cisco IPS Sensor performance? (Choose three.)
A. enable all anti-evasive measures to reduce noise
B. place the Cisco IPS Sensor behind a firewall
C. always enable unidirectional capture
D. disable unneeded signatures
E. have multiple Cisco IPS Sensors in the path and configure them to detect different types of events
F. enable selective packet capture using VLAN ACL on the Cisco IPS 4200 Series Sensors
Correct Answer: BDE Section: (none) Explanation
Explanation/Reference:
QUESTION 87
Select the two correct general Cisco IPS Sensor tuning recommendations if the environment consists exclusively of Windows servers. (Choose two.)
A. use “NT” IP fragment reassembly mode
B. use “Windows” TCP stream reassembly mode
C. disable deobfuscation for all HTTP signatures
D. enable all IIS signatures
E. enable all NFS signatures
F. enable all RPC signatures
Correct Answer: AD Section: (none) Explanation
Explanation/Reference:
QUESTION 88
Which of the following statements best describes how IP logging should be used?
A. only be used temporarily for such purposes as attack confirmation, damage assessment, or the collection of forensic evidence, because of its impact on performance
B. be used sparingly because there is a 4-GB limit on the amount of data that can be logged
C. always be enabled since it uses a FIFO buffer on the Cisco IPS Sensor flash memory
D. be used to automatically correlate events with Cisco Security MARS for incident PassGuide.com-Make You Succeed To Pass IT Exams PassGuide 642-533 investigations
E. only be used when you are also using inline IPS mode
Correct Answer: A Section: (none) Explanation
Explanation/Reference:
QUESTION 89
Which signature action or actions should be selected to cause the attacker’s traffic flow to terminate when the Cisco IPS Sensor is operating in promiscuous mode?
A. deny attacker
B. deny connection
C. deny packet
D. reset tcp connection
E. deny packet, reset tcp connection
F. deny connection, reset tcp connection
Correct Answer: D Section: (none) Explanation
Explanation/Reference:
QUESTION 90
Which Cisco IPS Sensor feature correlates events for more accurate detection of attacks, such as worms, that exploit a number of different vulnerabilities and can trigger several different signatures?
A. Analysis engine
B. SensorApp
C. Application Policy Enforcement
D. Summarizer
E. Normalizer
F. Meta Event Generator
Correct Answer: F Section: (none) Explanation
Explanation/Reference:
QUESTION 91
Refer to the exhibit. You are the security administrator for the network in the exhibit. You want your inline Cisco IPS sensor to drop packets that pose the most severe risk to your network, especially to the servers on your DMZ. Which two of the following parameters should you set to protect your DMZ servers in the most time-efficient manner? (Choose two.)
PassGuide.com-Make You Succeed To Pass IT Exams PassGuide 642-533
A. event action filter
B. signature fidelity rating
C. alert severity
D. event action override
E. application policy
F. target value rating
Correct Answer: DF Section: (none) Explanation
Explanation/Reference:
QUESTION 92
Which three of the following are tuning parameters that affect the Cisco IPS Sensor globally? (Choose three.)
A. IP logging
B. alert summarization
C. IP fragment reassembly
D. TCP stream reassembly
E. meta reset interval
F. alert frequency
Correct Answer: ACD Section: (none) Explanation
Explanation/Reference:
QUESTION 93
When signature 3116 fires, you want your Cisco IPS Sensor to terminate the current packet and future packets on this TCP flow only. Which action should you assign to the signature?
A. Deny Attacker Inline
B. Deny Connection Inline PassGuide.com-Make You Succeed To Pass IT Exams PassGuide 642-533
C. Reset TCP Connection
D. Request Block Connection
Correct Answer: B Section: (none) Explanation
Explanation/Reference:
QUESTION 94
How should you create a custom signature that will fire when a series of pre-defined signatures occur and you want the Cisco IPS Sensor to generate alerts only for the new custom signature, not for the individual signatures?
A. Use the Normalizer engine and remove the Produce Alert action from the component signatures.
B. Use the Meta engine and remove the Produce Alert action from the component signatures.
C. Use the Trojan engine and remove the Produce Alert action from the component signatures.
D. Use the ATOMIC engine and set the summary mode to Global Summarize.
E. Use the Normalizer engine and set the summary mode to Global Summarize.
F. Use the Service engine and set the summary mode to Global Summarize.
Correct Answer: B Section: (none) Explanation
Explanation/Reference:
QUESTION 95
Which statement is correct if “Use Threat Rating Adjustment” is enabled from the Event Action Rules > rules0 > General Settings menu?
A. The threat rating adjustment will be subtracted from the risk rating based on the action taken by the IPS sensor to produce the threat rating.
B. The risk rating will be adjusted by the addition of the threat rating adjustment based on the action taken by the Cisco IPS Sensor.
C. The threat rating adjustment will enable a fast way to add event actions based on the risk rating.
D. The threat rating adjustment will enable the Cisco IPS Sensor to adjust the risk rating based on the attack relevancy rating.
E. The threat rating adjustment will enable the Cisco IPS Sensor to adjust the risk rating based on the target value rating.
F. The threat rating adjustment will enable the Cisco IPS Sensor to adjust the risk rating based on the signature fidelity.
Correct Answer: A Section: (none) Explanation
Explanation/Reference:
QUESTION 96
You think users on your corporate network are disguising the use of file-sharing applications by tunneling the traffic through port 80. How can you configure your Cisco IPS Sensor to identify and stop this activity?
A. Enable all signatures in the Service HTTP engine.
B. Assign the Deny Packet Inline action to all signatures in the Service HTTP engine.
C. Enable all signatures in the Service HTTP engine. Then create an event action override that PassGuide.com-Make You Succeed To Pass IT Exams PassGuide 642-533 adds the Deny Packet Inline action to events triggered by these signatures if the traffic originates from your corporate network.
D. Enable the alarm for the non-HTTP traffic signature. Then create an Event Action Override that adds the Deny Packet Inline action to events triggered by the signature if the traffic originates from your corporate network.
E. Enable both the HTTP application policy and the alarm on non-HTTP traffic signature.
Correct Answer: E Section: (none) Explanation
Explanation/Reference:
QUESTION 97
Which statement accurately describes what the External Product Interface feature included in the Cisco IPS 6.0 software release allows the Cisco IPS Sensor to do?
A. collaborate with Cisco Security MARS for incident investigations
B. collaborate with Cisco Security Manager for centralized events management
C. have Cisco IEV subscribe to it and receive events from it
D. receive host postures and quarantined IP address events from the CiscoWorks Management Center for Cisco Security Agent
E. perform Anomaly Detection by receiving events from external sources
Correct Answer: D Section: (none) Explanation
Explanation/Reference:
QUESTION 98
You are configuring Cisco IPS Sensor Anomaly Detection and have just set the scanner threshold to 48. What will this accomplish?
A. If there are more than 48 unestablished connections from a single source to different destination IP addresses, an Anomaly Detection signature will be triggered.
B. If there are more than 48 sources generating at least one unestablished connection to different destination IP addresses, an Anomaly Detection signature will be triggered.
C. A maximum of 48 scanners can be present on the network before an Anomaly Detection signature will be triggered.
D. The scheduler will replace the knowledge base every 48 hours.
E. The histogram high threshold will be set to 48 destination IP addresses.
Correct Answer: A Section: (none) Explanation
Explanation/Reference: QUESTION 99
Which three statements accurately describe Cisco IPS 6.0 Sensor Anomaly Detection? (Choose three.)
A. It sub-divides the network into two zones (internal and external).
B. It is used to identify worms which spread by scanning the network.
C. In the Anomaly Detection histograms, the number of source IP addresses is either learned or configured by the user.
D. In the Anomaly Detection histograms, the number of destination IP addresses is predefined.
E. It has three modes: learn mode, detect mode, and attack mode. PassGuide.com-Make You Succeed To Pass IT Exams PassGuide 642-533
F. Anomaly Detection signatures have three sub-signatures (single scanner, multiple scanners, and worms outbreak).
Correct Answer: BCD Section: (none) Explanation
Explanation/Reference:
QUESTION 100
What is used to perform password recovery for the “cisco” admin account on a Cisco IPS 4200 Series Sensor?
A. setup mode
B. ROMMON CLI
C. GRUB menu
D. recovery partition
E. Cisco IDM
Correct Answer: C Section: (none) Explanation
Explanation/Reference:
QUESTION 101
Which statement accurately describes Cisco IPS Sensor automatic signature and service pack updates?
A. The Cisco IPS Sensor can automatically download service pack and signature updates from Cisco.com.
B. The Cisco IPS Sensor can download signature and service pack updates only from an FTP or HTTP server.
C. You must download service pack and signature updates from Cisco.com to a locally accessible server before they can be automatically applied to your Cisco IPS Sensor.
D. When you configure automatic updates, the Cisco IPS Sensor checks Cisco.com for updates hourly.
E. If multiple signature or service pack updates are available when the sensor checks for an update, the Cisco IPS Sensor installs the first update it detects.
Correct Answer: C Section: (none) Explanation
Explanation/Reference: QUESTION 102
In which three ways does a Cisco IPS network sensor protect the network from attacks? (Choose three.)
A. It uses a blend of intrusion detection technologies to detect malicious network activity.
B. It can generate an alert when it detects traffic that matches a set of rules that pertain to typical intrusion activity.
C. It permits or denies traffic into the protected network based on access lists that you create on the sensor.
D. It can take a variety of actions when it detects traffic that matches a set of rules that pertain to typical intrusion activity.
E. It uses behavior-based technology that focuses on the behavior of applications to protect network devices from known attacks and from new attacks for which there is no known PassGuide.com-Make You Succeed To Pass IT Exams PassGuide 642-533 signature.
F. It uses anomaly detection technology to prevent evasive techniques such as obfuscation, fragmentation, and encryption.
Correct Answer: ABD Section: (none) Explanation
Explanation/Reference:
QUESTION 103
Which one of the following statements is true regarding tuned signatures?
A. require that you create subsignatures that can then be tuned to your needs
B. require that you create custom signatures that can then be tuned to your needs
C. contain modified parameters of built-in signatures
D. begin with signature number 60000
E. are tuned using the Cisco IDM Custom Signature Wizard
Correct Answer: C Section: (none) Explanation
Explanation/Reference:
QUESTION 104
What two steps must you perform to initialize a Cisco IPS Sensor appliance? (Choose two.)
A. connect a serial cable to the console port of the sensor
B. connect to the sensor via SSH
C. use the Cisco IDM Setup Wizard
D. issue the setup command via the CLI
E. enable Telnet and then configure basic sensor parameters
Correct Answer: AD Section: (none) Explanation
Explanation/Reference:
QUESTION 105
Which two management access methods are enabled by default on a Cisco IPS Sensor? (Choose two.)
A. HTTP
B. HTTPS
C. IPsec
D. SSH
E. Telnet
Correct Answer: BD Section: (none) Explanation
Explanation/Reference:
QUESTION 106
You are using Cisco IDM. What precaution must you keep in mind when adding, editing, or deleting allowed hosts on a Cisco IPS Sensor?
A. You must not allow entire subnets to access the Cisco IPS Sensor
B. When using access lists to permit remote access, you must specify the direction of allowed communications.
C. You must not delete the IP address used for remote management. PassGuide.com-Make You Succeed To Pass IT Exams PassGuide 642-533
D. You can only configure the allowed hosts using the CLI.
E. You must use an inverse mask, such as 10.0.2.0 0.0.0.255, for the specified network mask for the IP address.
Correct Answer: C Section: (none) Explanation
Explanation/Reference:
QUESTION 107
Refer to the exhibit. Which interfaces are assigned to an inline VLAN pair?
A. GigabitEthernet0/1 with GigabitEthernet0/2
B. GigabitEthernet0/1 with GigabitEthernet0/3
C. GigabitEthernet0/2 with GigabitEthernet0/3
D. None in this virtual sensor
Correct Answer: D Section: (none) Explanation
Explanation/Reference:
QUESTION 108
Refer to the exhibit. Which of these statements is true concerning VLAN Pairs and the
PassGuide.com-Make You Succeed To Pass IT Exams PassGuide 642-533 GigabitEthernet0/0 interface?
A. To add another VLAN pair to interface GigabitEthernet0/0, you would need to edit the current configuration.
B. To add another VLAN pair to interface GigabitEthernet0/0, you would need to click the Add button and enter the appropriate information into the current configuration.
C. You cannot delete the default VLAN pair on interface GigabitEthernet0/0 subinterface 1.
D. You cannot add another VLAN pair to interface GigabitEthernet0/0 because it already has a pair assigned to it.
Correct Answer: B Section: (none) Explanation
Explanation/Reference:
QUESTION 109
Which two communication protocols does Cisco IEV support for communications with Cisco IPS Sensors? (Choose two.)
A. SSH
B. HTTP
C. HTTPS
D. IPsec
E. SCP
Correct Answer: BC Section: (none) Explanation
Explanation/Reference:
QUESTION 110
Which CLI mode allows you to tune signatures?
A. global configuration
B. service signature-definition
C. service analysis-engine
D. privileged exec
E. setup
F. virtual-sensor-configuration
Correct Answer: B Section: (none) Explanation
Explanation/Reference:
PassGuide.com-Make You Succeed To Pass IT Exams PassGuide 642-533
QUESTION 111
What is the best way to mitigate the risk that executable-code exploits will perform malicious acts such as erasing your hard drive?
A. assign deny actions to signatures that are controlled by the Trojan engines
B. assign the TCP reset action to signatures that are controlled by the Normalizer engine
C. enable blocking
D. enable application policy enforcement
E. assign blocking actions to signatures that are controlled by the State engine
Correct Answer: A Section: (none) Explanation
Explanation/Reference:
QUESTION 112
Which TCP stream reassembly mode disables TCP window-evasion checking?
A. Loose
B. Strict
C. Asymmetric
D. Symmetric
E. Disable
Correct Answer: C Section: (none) Explanation
Explanation/Reference:
QUESTION 113
Which character must precede a variable to indicate that you are using a variable rather than a string?
A. percent sign
B. dollar sign
C. ampersand
D. pound sign
E. asterisk
Correct Answer: B Section: (none) Explanation
Explanation/Reference:
QUESTION 114
Which three values are used to calculate the risk rating for an event? (Choose three.)
A. attack severity rating
B. fidelity severity rating
C. target fidelity rating
D. target value rating
E. signature fidelity rating
F. signature attack rating
Correct Answer: ADE Section: (none) Explanation
Explanation/Reference:
QUESTION 115
PassGuide.com-Make You Succeed To Pass IT Exams PassGuide 642-533
Which two of the following parameters affect the risk rating of an event? (Choose two.)
A. alert severity
B. global summary threshold
C. signature fidelity rating
D. scanner threshold
E. engine type
F. event count key
Correct Answer: AC Section: (none) Explanation
Explanation/Reference:
QUESTION 116
Refer to the exhibit. As an administrator, you need to change the Event Action and Event Count settings for signature 1108 in the sig1 instance. Which of the following should you select to view and change the required parameters?
A. Edit button
B. Actions button
C. Miscellaneous tab
D. Signature Variables tab
Correct Answer: A Section: (none) Explanation
Explanation/Reference:
PassGuide.com-Make You Succeed To Pass IT Exams PassGuide 642-533
QUESTION 117
You have been made aware of new and unwanted traffic on your network. You want to create a signature to monitor and perform an action against that traffic when certain thresholds are reached. What would be the best way to configure this new signature?
A. Edit a built-in signature that closely matches the traffic you are trying to prevent.
B. Clone and edit an existing signature that closely matches the traffic you are trying to prevent.
C. Use the Custom Signature Wizard.
D. Create a new signature definition, edit it, and then enable it.
E. Use the Anomaly Detection functions to learn about the unwanted traffic, then create a new Meta signature using Cisco IDM.
Correct Answer: C Section: (none) Explanation
Explanation/Reference:
QUESTION 118
You would like to have your inline sensor deny attackers inline when events occur that have risk ratings over 85. Which two actions, when taken in conjunction, will accomplish this? (Choose two.)
A. create target value ratings of 85 to 100
B. create an Event Action Filter, and assign the risk rating range of 85 to 100 to the filter
C. assign the risk rating range of 85 to 100 to the Deny Attacker Inline event action
D. enable event action overrides
E. create an event variable for the protected network
F. enable Event Action Filters
Correct Answer: CD Section: (none) Explanation
Explanation/Reference:
QUESTION 119
Refer to the exhibit. As a network administrator, you want to assign a target value rating to your network assets. Which menu tree path would you need to follow to reach a location from which you can configure the Target Value Rating parameter?
PassGuide.com-Make You Succeed To Pass IT Exams PassGuide 642-533
A. Analysis Engine > Virtual Sensors
B. Analysis Engine > Global Variables
C. Policies > Signature Definitions
D. Policies > Event Action Rules
E. Policies > Anomaly Detections
Correct Answer: D Section: (none) Explanation
Explanation/Reference:
QUESTION 120
You want to create multiple event filters that use the same parameter value. What would be the most efficient way to accomplish this task?
A. create a global variable
B. create a target value rating
C. create an event variable
D. clone and edit an event filter
Correct Answer: C Section: (none) Explanation
Explanation/Reference:
PassGuide.com-Make You Succeed To Pass IT Exams PassGuide 642-533
QUESTION 121
When configuring Passive OS Fingerprinting, what is the purpose of restricting operating system mapping to specific addresses?
A. excludes the defined IP addresses from automatic risk rating calculations so that you can specify the desired risk rating
B. allows you to configure separate OS maps within that IP address range
C. specifies which IP address range to import from the EPI for OS fingerprinting
D. limits the ARR to the defined IP addresses
Correct Answer: D Section: (none) Explanation
Explanation/Reference:
QUESTION 122
Which two statements accurately describe virtual sensor configuration? (Choose two.)
A. You must create a new instance of a signature set, such as sig1, and assign it to vs1.
B. The packet processing policy is virtualized.
C. Creating a new virtual sensor creates a “virtual” machine.
D. The sensor’s interfaces are virtualized.
E. You cannot delete vs0.
Correct Answer: BE Section: (none) Explanation
Explanation/Reference:
QUESTION 123
With Cisco IPS 6.0, what is the maximum number of virtual sensors that can be configured on a single platform?
A. the number depends on the amount of device memory
B. two in promiscuous mode using VLAN groups, four in inline mode supporting all interface type configurations
C. two
D. four
E. six
Correct Answer: D Section: (none) Explanation
Explanation/Reference:
QUESTION 124
Refer to the exhibit. Which further action must you take in order to create a new virtual sensor?
PassGuide.com-Make You Succeed To Pass IT Exams PassGuide 642-533
A. assign a unique name
B. create and assign a unique Signature Definition Policy
C. create and assign a unique Event Action Rule Policy
D. set AD Operational Mode to Inactive as that is a global parameter
E. set Inline TCP Session Tracking Mode to Interface Only as there is only one interface available for assignment
F. assign a description
Correct Answer: A Section: (none) Explanation
Explanation/Reference:
QUESTION 125
Refer to the exhibit. Based on this partial CLI output, what can be determined about anomaly detection?
PassGuide.com-Make You Succeed To Pass IT Exams PassGuide 642-533
A. Learning mode has expired and the sensor is running normally.
B. Learning mode has been manually disabled.
C. An attack is in progress and learning mode has been automatically disabled.
D. The virtual sensor vs1 has learned normal traffic patterns and is currently in detection mode.
Correct Answer: C Section: (none) Explanation
Explanation/Reference:
QUESTION 126
How can you clear events from the event store?
A. You do not need to clear the event store; it is a circular log file, so once it reaches the maximum size it will be overwritten by new events.
B. You must use the CLI clear events command.
C. If you have Administrator privileges, you can do this by selecting Monitoring > Events > Reset button in Cisco IDM.
D. You should select File > Clear IDM Cache in Cisco IDM.
E. You cannot clear events from the event store; they must be moved off the system using the copy command.
Correct Answer: B Section: (none) Explanation
Explanation/Reference:
QUESTION 127
Which action does the copy /erase ftp://172.26.26.1/sensor_config01 current-config command perform?
A. erases the sensor_config01 file on the FTP server and replaces it with the current configuration file from the Cisco IPS Sensor
B. copies and saves the running configuration to the FTP server and replaces it with the source configuration file
C. overwrites the backup configuration and applies the source configuration file to the system default configuration
D. merges the source configuration file with the current configuration
Correct Answer: C Section: (none) Explanation
Explanation/Reference: QUESTION 128
PassGuide.com-Make You Succeed To Pass IT Exams PassGuide 642-533
Which of the following is a valid file name for a Cisco IPS 6.0 system image?
A. IPS-K9-pkg-6.0-sys_img.sys
B. IPS-4240-K9-img-6.0-sys.sys
C. IPS-K9-cd-11-a-6.0-1-E1.img
D. IPS-4240-K9-sys-1.1-a-6.0-1-E1.img
Correct Answer: D Section: (none) Explanation
Explanation/Reference:
QUESTION 129
You would like to investigate an incident and have already enabled the Log Pair Packets action on various signatures being triggered. What should you do next?
A. Use CLI to send the IP log to a PC using TFTP, then open it with Notepad to view and interpret the contents.
B. Use Cisco Security Manager to retrieve the IP log then use the Cisco Security Manager IPS Manager to decode the IP log.
C. Use Cisco IDM to download the IP log to a management station then use a packet analyzer like Ethereal to decode the IP log.
D. Use Cisco IEV to retrieve the IP log then use the IEV Generate Reports function to produce a report based on the IP log content.
E. Use the External Product Interface feature to download the IP log to Cisco Security MARS for incident investigation.
Correct Answer: C Section: (none) Explanation
Explanation/Reference:
QUESTION 130
Refer to the exhibit. Based on the partial output shown, which of these statements is true?
A. The module installed in slot 1 needs to be a type 5540 module to be compatible with the PassGuide.com-Make You Succeed To Pass IT Exams PassGuide 642-533 ASA 5540 Adaptive Security Appliance module type.
B. The module installed in slot 1 needs to be upgraded to the same software revision as module 0 or it will not be recognized.
C. Module 0 system services are not running.
D. There is a Cisco IPS security services module installed.
Correct Answer: D Section: (none) Explanation
Explanation/Reference:
QUESTION 131
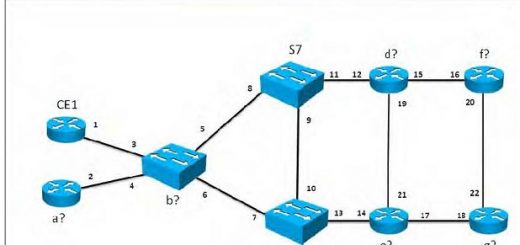
Topology
PassGuide.com-Make You Succeed To Pass IT Exams PassGuide 642-533
Case Study ( 6 Questions): A.
B.
C.
D.
Correct Answer: Section: (none) Explanation
Explanation/Reference:
QUESTION 132
Which two of the following statements are correct regarding the virtual sensors configurations on the IPS sensor? (Choose two.)
A. vs1 uses inline interface-pairs
B. vs1 operates inline between vlan 102 and vlan 201
C. vs1 uses the ad1 anomaly detection instance
D. vs0 uses inline mode
E. vs0 was created by the system administrator
F. vs0 and vs1 shares the same signature definition instance (vs0)
Correct Answer: BC Section: (none) Explanation
Explanation/Reference:
QUESTION 133
A single scanner needs to scan how many hosts belonging to the internal zone on TCP port 8081 before the anomaly detection configuration for vs1 will fire an alert?
PassGuide.com-Make You Succeed To Pass IT Exams PassGuide 642-533
A. 3 or more hosts
B. 6 or more hosts
C. 9 or more hosts
D. 150 or more hosts
E. 200 or more hosts
F. 250 or more hosts
Correct Answer: D Section: (none) Explanation
Explanation/Reference:
QUESTION 134
Referring to the configuration for vs1, the 172.26.26.51 host OS fingerprinting is manually configured as which operating system type?
A. Linux
B. AIX
C. Solaris
D. Windows
E. HP UX
F. Mac OS
Correct Answer: D Section: (none) Explanation
Explanation/Reference:
QUESTION 135
Which three of the following statements are correct regarding the IPS Sensor/CSAMC communications configurations? Choose three.)
A. The username used to login to the CSAMC is “testing”
B. TCP port 80 is used to communicate with the CSAMC
C. Watch list information is allowed to be passed from the CSAMC to the IPS sensor
D. Host Postures information is not allowed to be passed from the CSAMC to the IPS sensor
E. The 172.26.26.51 management station is the CSAMC
F. Any attacks triggered by a host on the watch list will have its risk rating decreased by 25
Correct Answer: ACE Section: (none) Explanation
Explanation/Reference:
Flydumps Cisco 642-533 Questions and Answers Products basically comprise of the simulated Cisco 642-533 exam questions AND their most correct answers, accompanied with a methodical elucidation of the Cisco 642-533 answers and the probable wrong answers.The extent to which Cisco 642-533 Questions and Answers Products cover their Cisco subject is so thorough, that once you are done with a Cisco product, passing the Cisco 642-533 exam in first attempt should be a piece of cake.