[New Questions] Best Cisco 400-201 Dumps CCIE SP Exam V4.1 Practice Test Video Questions With New Discount
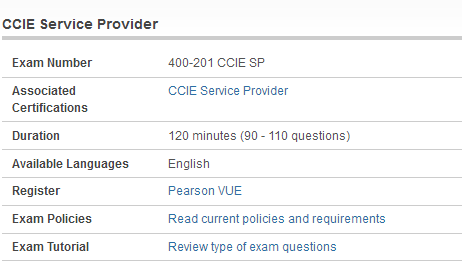
Are you still studying Cisco 400-201 dumps materials? The CCIE Service Provider Written Exam Version 4.1 (400-201 CCIE SP) exam is a 120 minutes (90 – 110 questions) assessment in pass4itsure that is associated with the CCIE Service Provider certification. “CCIE Service Provider Written Exam Version 4.1” is the exam name of Pass4itsure Cisco 400-201 dumps test which designed to help candidates prepare for and pass the Cisco 400-201 exam. If you have decided to participate in the Cisco 210-260 dumps training materials, Pass4itsure is here.
Best Cisco 400-201 dumps exam V4.1 CCIE Service Provider practice test video questions with new discount. We can help you achieve your goals. We know that you need to pass your Cisco https://www.pass4itsure.com/400-201.html dumps exam, we promise that provide high quality exam materials for you, Which can help you through Cisco 210-260 training materials.
[New Pass4itsure 400-201 Dumps Questions From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWV2ZxQlJ2OGxkaXc
[New Pass4itsure 300-115 Dumps Questions From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWLW41Sk5QSDdPTFU
Question No : 3 Select two valid administratively scoped multicast addresses in networks running Interior Gateway protocols like EIGRP and OSPF (Choose two).
A. 239.255.255.255
B. 224.0.0.10
C. 239.0.0.1
D. 224.0.0.5
400-201 exam Answer: A,C
Question No : 4 The product team at an ISP that offers VoIP services wants to add two-way video conferencing to their product offering. Which three QoS methods can be applied for real time traffic on WAN links with speeds that are slower than 768 Kbps? (Choose three.)
A. Apply voice-adaptive fragmentation to ensure that large video packets are fragmented and interleaved.
B. Apply LLQ with video traffic that is dedicated in the priority queue.
C. Apply MLP link fragmentation and interleaving to the interface.
D. Apply CBWFQ with video traffic in its own class, which is marked with aPHB value of AF41.
E. Apply CBWFQ with VoIP traffic in its own class, which is marked with aPHB value of EF.
F. Apply LLQ with both voice traffic and video traffic in the same priority queue
Answer: C,D,E
Question No : 5 An engineer is deploying RTBH. What is necessary routing constraint required for successful implementation?
A. The trigger device must have an iBGP session with all the clusters/route reflectors in the autonomous system.
B. The trigger device must redistribute the static route pointing to a null interface into the IGP process.
C. The no ip reachables command must be issued on the PE router interface under attack.
D. The attacker’s destination IP address must be routed to a null interface.
E. The eBGP sessions need to set the next-hop attribute value to the trigger device loopback interface.
400-201 dumps Answer: A
Explanation: Explanation :
Question No : 8 Where are MPLS point-to-multipoint traffic engineering packets replicated?
A. head-end router
B. branch-point router
C. midpoint router
D. leaf-point router
E. tail-end router
Answer: B
Question No : 9 Retaining LDP session if one links fail out of two for two neighbors.
A. MPLS LDP targeted-hello accept
B. MPLS LDP sync
C. MPLS IP
D. MPLS LDP autoconfig
400-201 pdf Answer: B
Explanation:
QUESTION 10
FITSAF stands for Federal Information Technology Security Assessment Framework. It is a methodology for assessing the security of information systems. Which of the following FITSAF levels shows that the procedures and controls have been implemented?
A. Level 4
B. Level 1
C. Level 3
D. Level 5
E. Level 2
Correct Answer: C
QUESTION 11
Certification and Accreditation (C&A or CnA) is a process for implementing information security. Which of the following is the correct order of C&A phases in a DITSCAP assessment?
A. Definition, Validation, Verification, and Post Accreditation
B. Verification, Definition, Validation, and Post Accreditation
C. Verification, Validation, Definition, and Post Accreditation
D. Definition, Verification, Validation, and Post Accreditation
400-201 vce Correct Answer: D
QUESTION 12
System Authorization is the risk management process. System Authorization Plan (SAP) is a comprehensive and uniform approach to the System Authorization Process. What are the different phases of System Authorization Plan? Each correct answer represents a part of the solution. Choose all that apply.
A. Post-Authorization
B. Pre-certification
C. Post-certification
D. Certification
E. Authorization
Correct Answer: ABDE
QUESTION 13
Certification and Accreditation (C&A or CnA) is a process for implementing information security. It is a systematic procedure for evaluating, describing, testing, and authorizing systems prior to or after a system is in operation. Which of the following statements are true about Certification and Accreditation? Each correct answer represents a complete solution. Choose two.
A. Accreditation is the official management decision given by a senior agency official to authorize operation of an information system.
B. Accreditation is a comprehensive assessment of the management, operational, and technical security controls in an information system.
C. Certification is the official management decision given by a senior agency official to authorize operation of an information system.
D. Certification is a comprehensive assessment of the management, operational, and technical security controls in an information system.
400-201 exam Correct Answer: AD
QUESTION 14
Which of the following requires all general support systems and major applications to be fully certified and accredited before these systems and applications are put into production? Each correct answer represents a part of the solution. Choose all that apply.
A. NIST
B. FIPS
C. FISMA
D. Office of Management and Budget (OMB)
Correct Answer: CD
QUESTION 15
The National Information Assurance Certification and Accreditation Process (NIACAP) is the minimum standard process for the certification and accreditation of computer and telecommunications systems that handle U.S. national security information. What are the different types of NIACAP accreditation? Each correct answer represents a complete solution. Choose all that apply.
A. Secure accreditation
B. Type accreditation
C. System accreditation
D. Site accreditation
400-201 dumps Correct Answer: BCD
QUESTION 16
According to U.S. Department of Defense (DoD) Instruction 8500.2, there are eight Information Assurance (IA) areas, and the controls are referred to as IA controls. Which of the following are among the eight areas of IA defined by DoD? Each correct answer represents a complete solution. Choose all that apply.
A. VI Vulnerability and Incident Management
B. DC Security Design & Configuration
C. EC Enclave and Computing Environment
D. Information systems acquisition, development, and maintenance
Correct Answer: ABC
QUESTION 17
DIACAP applies to the acquisition, operation, and sustainment of any DoD system that collects, stores, transmits, or processes unclassified or classified information since December 1997. What phases are identified by DIACAP? Each correct answer represents a complete solution. Choose all that apply.
A. Validation
B. Re-Accreditation
C. Verification
D. System Definition
E. Identification
F. Accreditation
400-201 pdf Correct Answer: ABCD
QUESTION 18
Which of the following is a subset discipline of Corporate Governance focused on information security systems and their performance and risk management?
A. Lanham Act
B. ISG
C. Clinger-Cohen Act
D. Computer Misuse Act
Correct Answer: B
QUESTION 19
Ben is the project manager of the YHT Project for his company. Alice, one of his team members, is confused about when project risks will happen in the project. Which one of the following statements is the most accurate about when project risk happens?
A. Project risk can happen at any moment.
B. Project risk is uncertain, so no one can predict when the event will happen.
C. Project risk happens throughout the project execution.
D. Project riskis always in the future.
400-201 vce Correct Answer: D
QUESTION 20
You are the project manager of the NKJ Project for your company. The project’s success or failure will have a significant impact on your organization’s profitability for the coming year. Management has asked you to identify the risk events and communicate the event’s probability and impact as early as possible in the project. Management wants to avoid risk events and needs to analyze the cost-benefits of each risk event in this project. What term is assigned to the low-level of stakeholder tolerance in this project?
A. Risk avoidance
B. Mitigation-ready project management
C. Risk utility function
D. Risk-reward mentality
Correct Answer: C
QUESTION 21. Which statement is true about conversion of a block storage database to an aggregate storage database?
A. Converted outlines are only written to the file system.
B. During the outline conversion process, shared members are removed from the outline.
C. Interactive mode conversion lets you alter hierarchy tags and change other member properties.
D. To facilitate write-back, you can create replicated partitions between block and aggregate storage databases.
400-201 exam Answer: C
QUESTION 22. Which two commands should be used in a report script to optimize data export? (Choose two.)
A. <SORTLEVEL>
B. {OUTALTNAMES\\}
C. {SUPZEROROWS\\}
D. {SUPMISSINGROWS\\}
Answer: CD
QUESTION 23. Which three settings in the essbase.cfg file must be set to configure a multiple instance of an Analytic Server? (Choose three.)
A. PORTBEGIN
B. AGENTPORT
C. SERVERPORTEND
D. AGENTPORTBEGIN
E. SERVERPORTBEGIN
400-201 dumps Answer: BCE
QUESTION 24. Which statement about connection pools is correct?
A. Connection pools are defined at the application server level.
B. A connection pool is required to be defined against a cluster.
C. All users in a single connection pool can have different Essbase security filter access.
D. A connection pool contains only one user ID and password when accessing Essbase.
Answer: D
QUESTION 25. In the Member Selection Dialog available in the Essbase Spreadsheet Add-in, what should you use to select members based on User Defined Attributes (UDA) and Attribute dimensions?
A. Find
B. Subset
C. Generation Name
D. Member Information
400-201 pdf Answer: B
QUESTION 26. Which three storage kernel features do aggregate storage databases support? (Choose three.)
A. dense data
B. sparse data
C. rapid aggregation
D. optimized to support high dimensionality
E. multiple blocks defined by Dense and Sparse dimensions and their members, optimized for financial
applications
Answer: BCD
QUESTION 27. What are two methods to optimize a block storage dataload? (Choose two.)
A. add to existing values
B. use commas for field delimiters
C. place a Dense dimension across columns
D. sort data file in order by Sparse dimensions
400-201 vce Answer: CD
QUESTION 28. Which dimension is typically the anchor dimension when optimizing Calculator Cache?
A. largest dense
B. largest sparse
C. smallest dense
D. smallest sparse
Answer: B
QUESTION 29. Which statement about index value pair compression is true?
A. Once selected, index value pair applies to all blocks.
B. Index value pair is the most effective in cubes with large, sparse blocks.
C. Index value pair is applied in Essbase Administration Services, Database Properties, Storage tab.
D. Index value pair reviews each block and evaluates the following compression types for highest
compression: RLE,bitmap, ZLIB or index value pair.
400-201 exam Answer: B
QUESTION 30. Which statement about Dynamic Time Series is true?
A. It provides to-date functionality.
B. It performs stored consolidations.
C. It allows for Dynamic Time dimension builds.
D. It creates alternate alias table(s) based on a Time dimension.
Answer: A


The Cisco CCIE Service Provider Written Exam (400-201) version 4.0 is a two-hour test with 90-110 questions that validate professionals who have the 400-201 dumps expertise to design, implement, diagnose, and troubleshoot complex Service Provider highly available network infrastructure and services based on dual stack solutions (IPv4 and IPv6); understand how the network and service components interoperate; and understand the functional https://www.pass4itsure.com/400-201.html dumps requirements and translate into specific device configurations.